I recently set out to upgrade a virtual host server from VMware Server to Oracle’s VirtualBox. The upgrade was a huge success. This is one of several articles where I talk about various aspects of that upgrade, hopefully helping others along the way. You might want to go back and read the introductory article Virtualization Revisited. Added 5-May-2011: Originally written using Ubuntu Server 10.04, this configuration also works without change on Ubuntu Server 11.04.
One of the things that I wanted from the new VM host was alerts for anomalous situations. Manually polling for trouble begins as a noble effort but trust me – after a while you’ll stop looking. About a year ago I was almost caught by a failing hard drive in a RAID array. Even after that incident, within a month or two I had pretty much stopped paying regular attention.
While setting up monitor/alert mechanisms on an old Windows server is quite the pain in the ass it’s a snap on Linux. Delivery of alerts and status reports via email is just perfect for me. All I wanted was the ability to have the system generate SMTP traffic; no messages would ever be received by the system. To prepare for that I set up a send-only email account to use the SMTP server on one of my domains solely for the VM host’s use as a mail relay. Then I got on with configuring Postfix, the standard Ubuntu mailer – one of several excellent sendmail alternatives.
Now maybe I’m just a dummy, but I found various aspects of the Postfix and related configurations to be a little tricky. Hence this article, which details what worked for me – and should work for you, too.
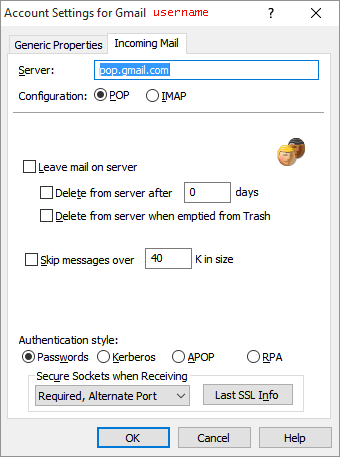
(In the stuff that follows, my example machine is named foo and it’s on an internal TLD called wan. My example machine’s system administrator account is sysadmin. My SMTP server is on mail.example.com listening on port 1212. The SMTP account is username with a password of yourpassword.)
Getting Started – Basic Configuration
Begin by installing Postfix, as you would any package.
$ sudo apt-get install postfix
For now, just hit Enter through the install questions. We’ll configure it properly following the install. You’ll be asked for the general type of mail configuration and Internet Site will be the default. Accept that by pressing Enter. You’ll be asked for the System mail name and something will probably be pre-filled. Accept that, too.
Now, go back and do a proper basic configuration.
$ sudo dpkg-reconfigure postfix
Several questions will follow. Here’s how to respond.
For the general type of mail configuration choose Internet Site.
Set the domain name for the machine. The panel provides a good explanation of what’s needed here, and chances are good that it’s pre-filled correctly. By example, foo.wan.
Provide the username of the system administrator. The panel provides a good explanation of what’s needed here. Use the name of the account that you specified when you installed Ubuntu. By example, sysadmin.
Provide a list of domains for which the machine should consider itself the final destination. The panel provides an OK explanation and it’s probably already pre-filled more-or-less correctly. But look carefully at the list that appears in the panel and edit it if it has obvious errors like extra commas. Again, using my example machine, a list like this is appropriate:
foo.wan, localhost.wan, localhost
You’ll be asked whether or not to force synchronous updates on the mail queue. Answer No, which is likely the default.
Next, specify the network blocks for which the host should relay mail. This entry is pre-filled based on the connected subnets. Unless you’ll be using an external SMTP server that requires it, you can simply remove all of the IPv6 stuff that appears here, leaving only the IPv4 entry which will probably look something like this:
127.0.0.0/8
Specify the mailbox size limit. The default is zero, meaning no limit. Accept that. Remember, all we’re planning to do is send mail, not receive it.
Set the character used to define a local address extension. The default is +. Accept it.
Choose the Internet protocols to use. Again, keeping with our earlier IPv4 decision select ipv4 from the list and accept it.
That’s it for the basic Postfix configuration! Next you’ll configure Postfix to do SMTP AUTH using SASL (saslauthd).
SMTP AUTH using SASL (saslauthd)
Since there are several commands to issue as root it’s convenient to sudo yourself as root to save some typing. Good practice dictates you should logout the root account just as soon as you’re finished.
Be careful. In this list of commands there is one – it sets smtpd_recipient_restrictions – that is quite long and may have wrapped on your display. Be sure to issue the entire command.
$ sudo -i
# postconf -e 'smtpd_sasl_local_domain ='
# postconf -e 'smtpd_sasl_auth_enable = yes'
# postconf -e 'smtpd_sasl_security_options = noanonymous'
# postconf -e 'broken_sasl_auth_clients = yes'
# postconf -e 'smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination'
# postconf -e 'inet_interfaces = all'
# echo 'pwcheck_method: saslauthd' >> /etc/postfix/sasl/smtpd.conf
# echo 'mech_list: plain login' >> /etc/postfix/sasl/smtpd.conf
Then press ctrl-D to logout the root account.
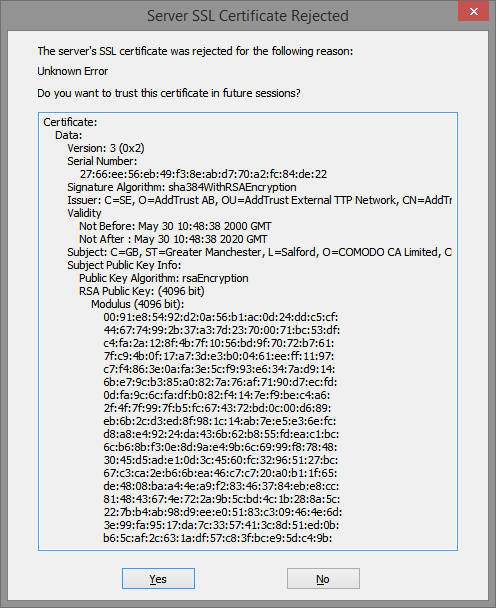
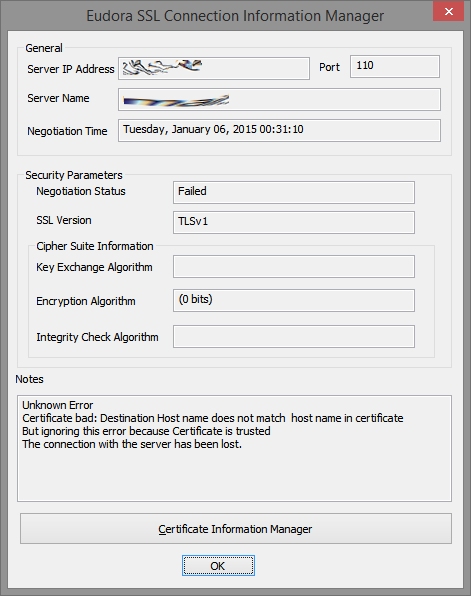
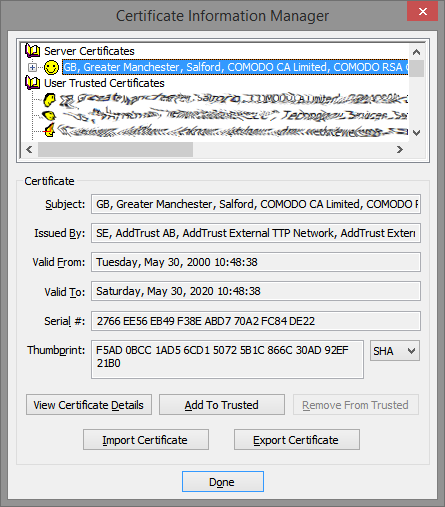
The next step is to configure the digital certificate for TLS.
Configure the Digital Certificate for TLS
Some of the commands that follow will ask questions. Follow these instructions and answer appropriately, modifying your answers to suit your situation. As earlier, sudo yourself to root and logout from root when finished.
$ sudo -i
# openssl genrsa -des3 -rand /etc/hosts -out smtpd.key 1024
You’ll be asked for the smtpd.key passphrase. Enter one and remember it. You’ll need to type it twice, as is customary when creating credentials. Then continue.
# chmod 600 smtpd.key
# openssl req -new -key smtpd.key -out smtpd.csr
You’ll be asked for your smtpd.key passphrase. Enter it.
Next you’ll be asked a series of questions that will make up a Distinguished Name, which is incorporated into your certificate. There’s much you can leave blank by answering with a period only. Here’s a sample set of responses (underlined) based on my US location and example system.
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Texas
Locality Name (eg, city) []:.
Organization Name (eg, company) [Internet Widgits Pty Ltd]:.
Organizational Unit Name (eg, section) []:.
Common Name (eg, YOUR name) []:Rick
Email Address []:sysadmin@foo.wan
A challenge password []:some-challenge-password
An optional company name []:.
Then continue.
# openssl x509 -req -days 3650 -in smtpd.csr -signkey smtpd.key -out smtpd.crt
You’ll be prompted for your smtpd.key passphrase. Enter it.
Then continue.
# openssl rsa -in smtpd.key -out smtpd.key.unencrypted
You’ll be prompted for your smtpd.key passphrase. Enter it.
Then continue.
# mv -f smtpd.key.unencrypted smtpd.key
# openssl req -new -x509 -extensions v3_ca -keyout cakey.pem -out cacert.pem -days 3650
You’ll be asked for a PEM passphrase. Enter one and remember it. You’ll need to type it twice, as is customary when creating credentials.
Like earlier, you’ll be asked a series of questions that will make up a Distinguished Name, which is incorporated into your certificate. There’s much you can leave blank by answering with a period only. Here’s a sample set of responses (underlined) based on my US location and example system.
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Texas
Locality Name (eg, city) []:.
Organization Name (eg, company) [Internet Widgits Pty Ltd]:.
Organizational Unit Name (eg, section) []:.
Common Name (eg, YOUR name) []:Rick
Email Address []:sysadmin@foo.wan
Next, issue the remaining commands.
# mv smtpd.key /etc/ssl/private/
# mv smtpd.crt /etc/ssl/certs/
# mv cakey.pem /etc/ssl/private/
# mv cacert.pem /etc/ssl/certs/
Then press ctrl-D to logout the root account.
Whew! We’ll continue by configuring Posfix to do TLS encryption for both incoming and outgoing mail (even though we’re only planning on sending mail at this point).
Configure Postfix to Do TLS Encryption
As earlier, sudo yourself to root and logout from root when finished.
$ sudo -i
# postconf -e 'smtpd_tls_auth_only = no'
# postconf -e 'smtp_use_tls = yes'
# postconf -e 'smtpd_use_tls = yes'
# postconf -e 'smtp_tls_note_starttls_offer = yes'
# postconf -e 'smtpd_tls_key_file = /etc/ssl/private/smtpd.key'
# postconf -e 'smtpd_tls_cert_file = /etc/ssl/certs/smtpd.crt'
# postconf -e 'smtpd_tls_CAfile = /etc/ssl/certs/cacert.pem'
# postconf -e 'smtpd_tls_loglevel = 1'
# postconf -e 'smtpd_tls_received_header = yes'
# postconf -e 'smtpd_tls_session_cache_timeout = 3600s'
# postconf -e 'tls_random_source = dev:/dev/urandom'
This next configuration command sets the host name, and this one uses my example machine’s host name. You should use your own instead.
# postconf -e 'myhostname = foo.wan'
Then press ctrl-D to logout the root account.
The postfix initial configuration is complete. Run the following command to start the Postfix daemon:
$ sudo /etc/init.d/postfix start
The Postfix daemon is now installed, configured and runing. Postfix supports SMTP AUTH as defined in RFC2554. It is based on SASL. It is still necessary to set up SASL authentication before you can use SMTP.
Setting Up SASL Authentication
The libsasl2-2 package is most likely already installed. If you’re not sure and want to try to install it you can, no harm will occur. Otherwise skip this command and simply continue.
$ sudo apt-get install libsasl2-2
Let’s continue the SASL configuration.
$ sudo mkdir -p /var/spool/postfix/var/run/saslauthd
$ sudo rm -rf /var/run/saslauthd
Create the file /etc/default/saslauthd.
$ sudo touch /etc/default/saslauthd
Use your favorite editor to edit the new file so that it contains the lines which follow. Just to be clear, the final line to add begins with “MECHANISMS=“.
# This needs to be uncommented before saslauthd will be run
# automatically
START=yes
PWDIR="/var/spool/postfix/var/run/saslauthd"
PARAMS="-m ${PWDIR}"
PIDFILE="${PWDIR}/saslauthd.pid"
# You must specify the authentication mechanisms you wish to use.
# This defaults to "pam" for PAM support, but may also include
# "shadow" or "sasldb", like this:
# MECHANISMS="pam shadow"
MECHANISMS="pam"
Save the file.
Next, update the dpkg state of /var/spool/portfix/var/run/saslauthd. The saslauthd init script uses this setting to create the missing directory with the appropriate permissions and ownership. As earlier, sudo yourself to root and logout from root when finished. Be careful, that’s another rather long command that may have wrapped on your display.
$ sudo -i
# dpkg-statoverride --force --update --add root sasl 755 /var/spool/postfix/var/run/saslauthd
Then press ctrl-D to logout the root account.
Test using telnet to connect to the running Postfix mail server and see if SMTP-AUTH and TLS are working properly.
$ telnet foo.wan 25
After you have established the connection to the postfix mail server, type this (substituting your server for mine, of course):
ehlo foo.wan
If you see the following lines (among others) then everything is working perfectly.
250-STARTTLS
250-AUTH LOGIN PLAIN
250-AUTH=LOGIN PLAIN
250 8BITMIME
Close the connection and exit telnet with this command.
quit
We’re almost there, promise.
Setting External SMTP Server Credentials
Remember, we set out to use an external Internet-connected SMTP server as a mail relay and this is how that is set up. I mentioned at the beginning of the article that I had set up a dedicated account on one of my domains. You might use one on your ISP. I would not, however, use your usual email account.
You’ll need to manually edit the /etc/postfix/main.cf file to add these lines:
smtp_sasl_auth_enable = yes
smtp_sasl_security_options = noanonymous
smtp_sasl_password_maps = hash:/etc/postfix/saslpasswd
smtp_always_send_ehlo = yes
relayhost = [mail.example.com]:1212
Of course, you’ll modify the relayhost = line to specify your external SMTP server. If you don’t need a port number then simply leave off the colon and port number following the closing bracket. I included the port number as a syntax example in case you needed to use one.
Did you notice the hash file mentioned in the lines you just added to/etc/postfix/main.cf? It holds the SMPT server logon credentials, and it’s time to create it.
$ sudo touch /etc/postfix/saslpasswd
Use your favorite editor to edit the file, adding the credentials with a line like this:
mail.example.com username@example.com:yourpassword
The components of the line you’re putting in the new file should be obvious.
(Before you cry foul… Yes, I’m well aware of the risk of storing credentials in the clear. It’s a manageable risk to me in this case for the following reasons. The physical machine is under my personal physical control. The credentials are dedicated to this single purpose. If the server becomes compromised I can disable the credentials from anywhere in the world I can obtain an Internet connection. If I’m dead and can’t do that, well, I guess it’s SEP and my incremental contribution to the SPAM of the world will torment my soul until the end of time. Your situation may be different and I leave it to you to secure the credentials.)
Anyway, before postfix can use that horribly insecure file it needs to be hashed by postmap:
$ sudo postmap /etc/postfix/saslpasswd
With that done, restart postfix.
$ sudo /etc/init.d/postfix restart
Applications that know how will now be able to generate mail but it’ll be convenient to be able to do it from the command line. Besides making testing of this configuration easier you’ll then be able to have your own scripts send messages with ease. For that you’ll need just one more package.
Installing the mailutils Package
Simple. Install the mailutils package.
$ sudo apt-get install mailutils
That’s it!
Try test sending some email from the command line. Substitute the address at which you usually receive mail for my example youraddress@yourserver.com.
$ echo "body: outbound email test" | mail -s "Test Subject" youraddress@yourserver.com
Check your inbox.
Wrapping Up
Well, that wasn’t so bad.



 Introduction
Introduction
 Unix, drop-in, and run. I never looked back. Since then I’ve developed a rather extensive set of filters and such to efficiently manage dozens of email accounts and tens of GB of messages.
Unix, drop-in, and run. I never looked back. Since then I’ve developed a rather extensive set of filters and such to efficiently manage dozens of email accounts and tens of GB of messages.